We've cooked up a bunch of improvements designed to reduce friction and make the.


Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
Unordered list
Bold text
Emphasis
Superscript
Subscript
We've released an expansion to our handling of API keys on Runpod. Previously, you were able to create API keys with read or read and write permissions, but now you can scope keys by endpoint and have more fine-grained control over what your keys allow access to. Here's a TL;DR summary of new features available with the update:
All of your existing keys will continue to function as they have been, so if you don't have a need for the new features, you can keep using your existing keys without issue. If any of this sounds useful to you, read on for the scoop!
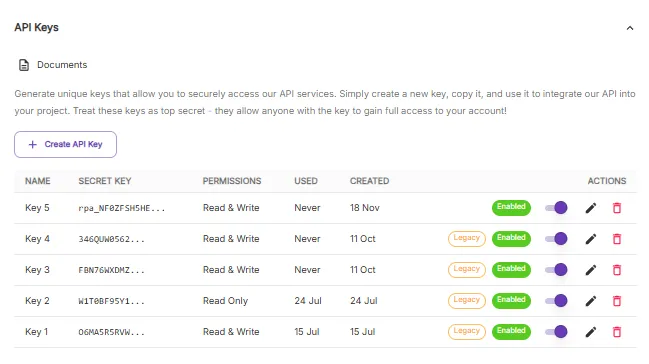
Your keys are in the same spot they have been, under your Settings page. All existing keys have already been migrated and will remain in their legacy format without any additional features, so to begin using the new features you'll need to create some new keys. Any new keys will be created with an rpa_ prefix. You can also enable or disable any key (legacy or not) with the slider.
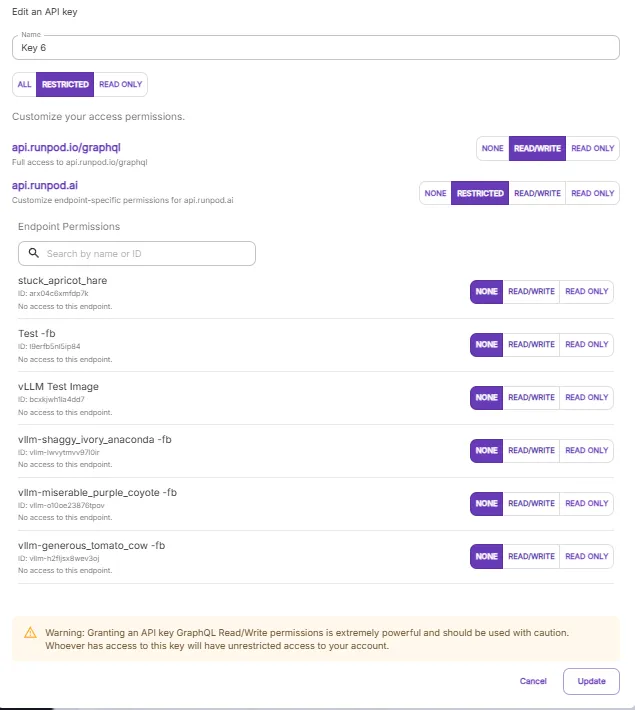
There are two main level of permissions at play here:
We released this because while API keys are a very powerful feature, they are also a direct link to your account, and by extension your account balance. This is especially true with GraphQL permissions; theoretically a leaked key could allow a user to create pods under your account for nefarious means (e.g. Bitcoin mining for profit on your dime.) No one wants that, so we want to ensure that you have as many options as possible to manage your account's security. We highly suggest you always follow the principle of least privilege when doling out access in general, and most specifically never allow read/write GraphQL access for longer or for more individuals than you absolutely need.
Questions? Feel free to pop on our Discord or ask our support team!



Runpod now supports scoped API keys with per-endpoint access, usage tracking, and on/off toggles. Create safer, more flexible keys that align with the principle of least privilege.

We've released an expansion to our handling of API keys on Runpod. Previously, you were able to create API keys with read or read and write permissions, but now you can scope keys by endpoint and have more fine-grained control over what your keys allow access to. Here's a TL;DR summary of new features available with the update:
All of your existing keys will continue to function as they have been, so if you don't have a need for the new features, you can keep using your existing keys without issue. If any of this sounds useful to you, read on for the scoop!
Your keys are in the same spot they have been, under your Settings page. All existing keys have already been migrated and will remain in their legacy format without any additional features, so to begin using the new features you'll need to create some new keys. Any new keys will be created with an rpa_ prefix. You can also enable or disable any key (legacy or not) with the slider.

There are two main level of permissions at play here:

We released this because while API keys are a very powerful feature, they are also a direct link to your account, and by extension your account balance. This is especially true with GraphQL permissions; theoretically a leaked key could allow a user to create pods under your account for nefarious means (e.g. Bitcoin mining for profit on your dime.) No one wants that, so we want to ensure that you have as many options as possible to manage your account's security. We highly suggest you always follow the principle of least privilege when doling out access in general, and most specifically never allow read/write GraphQL access for longer or for more individuals than you absolutely need.
Questions? Feel free to pop on our Discord or ask our support team!
The most cost-effective platform for building, training, and scaling machine learning models—ready when you are.
